Verify MAC of device, if approved user can connect
MAC not verified, user required to enter password
MAC not verified, user required to 2FA with OTP
Verify MAC of device, user required to enter password
Verify MAC of device, user required to 2FA with OTP
Specify allowed network IP range
Specify blocked network IP range
Specify allowed Internet public IP’s /domains
Specify blocked Internet public IP’s /domains
Website category filtering
Log identified devices requesting authentication
Log unidentified devices
Log failed authentications
Alert admin on a device failure
List the authenticated users
List IP requests not authenticated
Alert admin unknown MAC IP request
Failed authentication, alert admin
Network performance report
The A300 has 300Mb/s throughput and does not have a limit for the number of people and devices that can be authenticated.
The number of people that can be connected
to the network depends on the data traffic volume required for the business operations.
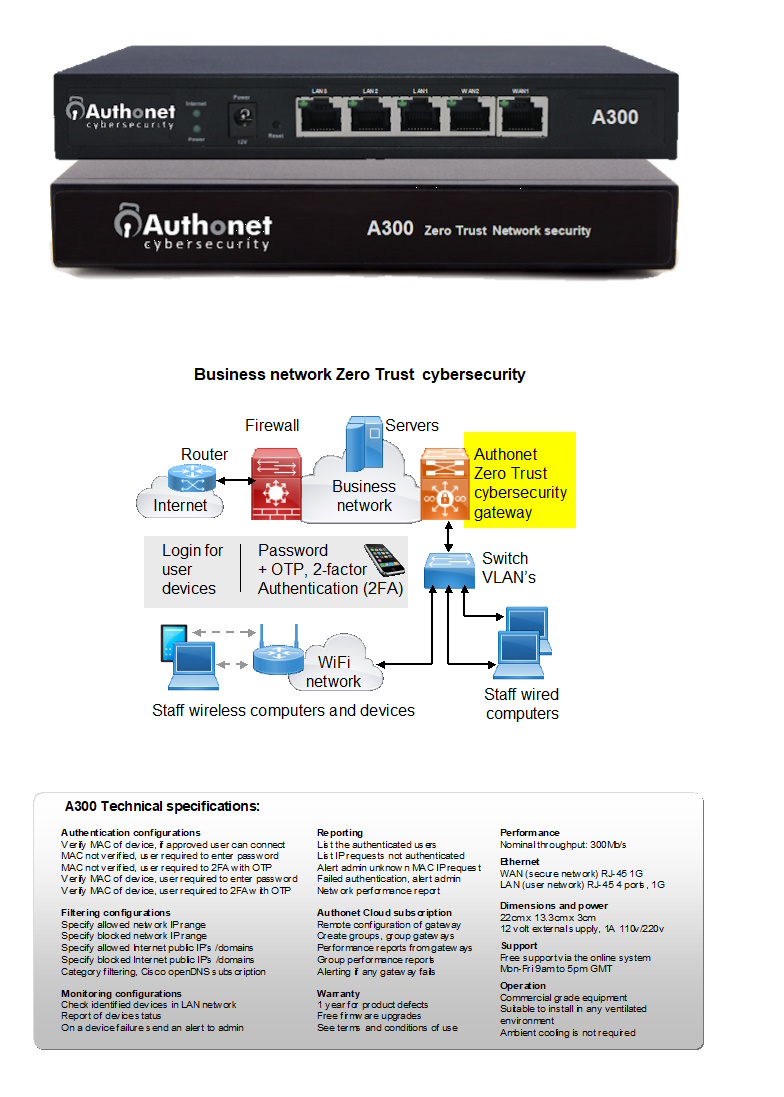
The Authonet Zero Trust cybersecurity gateway controls and monitors the connection of devices and users to the network where 75% of cyber attacks originate. The Authonet gateway ensures that only approved devices and users can connect to the network. User authentication includes multi-factor authentication. The Authonet Zero Trust gateway also determines what the user can and cannot access both in the local area network, and in the Internet. Authonet has a subscription cloud management and monitoring service that IT service providers use to provide security surveillance for their customers.
Verify MAC of device, if approved user can connect
MAC not verified, user required to enter password
MAC not verified, user required to 2FA with OTP
Verify MAC of device, user required to enter password
Verify MAC of device, user required to 2FA with OTP
Specify allowed network IP range
Specify blocked network IP range
Specify allowed Internet public IP’s /domains
Specify blocked Internet public IP’s /domains
Website category filtering
Log identified devices requesting authentication
Log unidentified devices
Log failed authentications
Alert admin on a device failure
List the authenticated users
List IP requests not authenticated
Alert admin unknown MAC IP request
Failed authentication, alert admin
Network performance report
The A1000 has 1Gb/s throughput and does not have a limit for the number of people and devices that can be authenticated.
The number of people that can be connected
to the network depends on the data traffic volume required for the business operations.
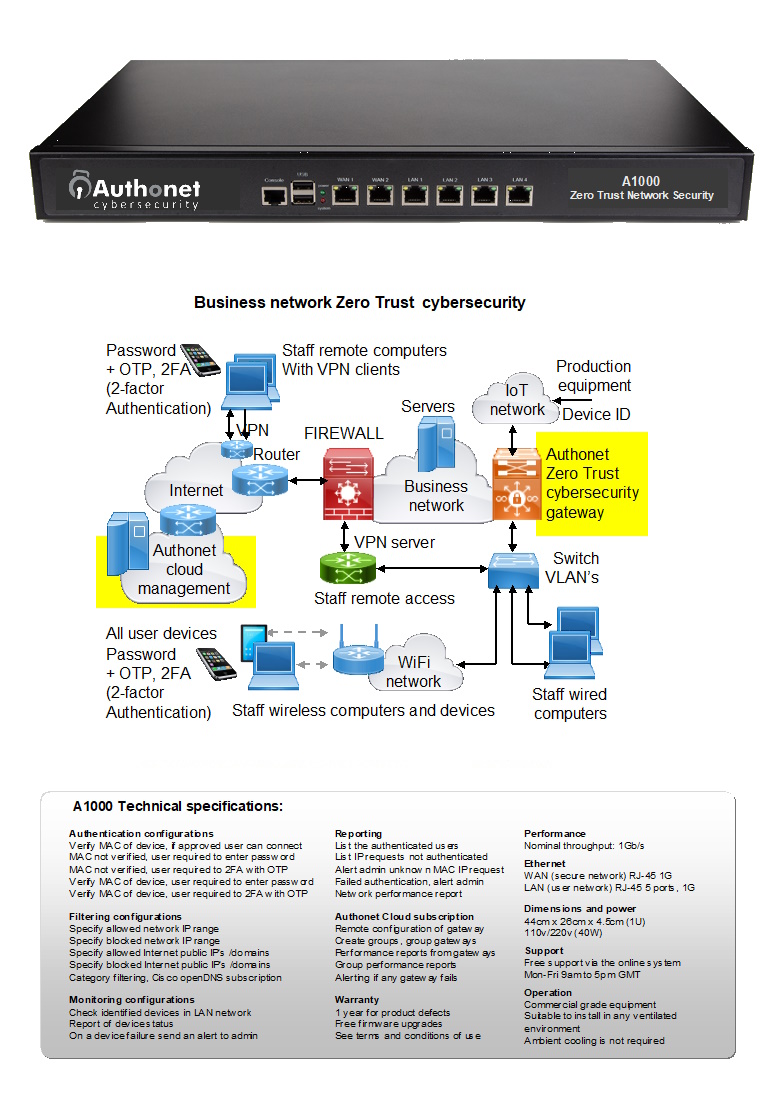
The Authonet Zero Trust cybersecurity gateway controls and monitors the connection of devices and users to the network where 75% of cyber attacks originate. The Authonet gateway ensures that only approved devices and users can connect to the network. User authentication includes multi-factor authentication. The Authonet Zero Trust gateway also determines what the user can and cannot access both in the local area network, and in the Internet. Authonet has a subscription cloud management and monitoring service that IT service providers use to provide security surveillance for their customers.
The Authonet Zero Trust Network Access (ZTNA) cybersecurity gateway features are configured using the software contained in each product. The management software is accessed by connecting a computer Ethernet connection to the administrator port, LAN4.